A recent case was unusual because most of the ipoc were located by the police examiner in a folder entitled MessengerCache at the path C:\Users\<user_name>\AppData\Local\Temp\MessengerCache.
My mission was to have a closer look at how this folder is utilised by the program Windows Live Messenger. The folder is a hidden folder and is used for various purposes by WLM. I found that the folder can be used to store the user tile (this may be an icon or a thumbnail photograph or graphic) and theme picture of a remote contact. Of course the remote user (who could be anywhere in the world) can change these at any time to a contraband image. In Figure 1 below the screenshot shows the Windows Live Messenger program running upon the local user’s computer. The two photographs arrowed and labelled as Remote User Tile and Remote User Theme Picture respectively have been received from the remote user Mars with whom the local user is engaged in an instant messaging conversation.
It is also possible for a remote contact anywhere in the world whilst engaged in an instant messaging conversation with the local user to drag a picture file into the conversation window. This results in the picture concerned appearing in the local user’s conversation window in full size and thumbnail form and at the same time a copy of the picture and a thumbnail version are stored within the MessengerCache folder. In the case that the picture concerned was ipoc the local user’s only immediate option would be to close the conversation window. He would be unlikely to be aware that the photograph concerned was now stored upon his own computer in the MessengerCache folder. In figure 2 the screenshot shows the local user’s conversation window after the remote user Mars has dragged a photograph of tulips into his conversation window. This has caused the local user’s conversation window to also display the tulip pictures. The tulip photograph would also be stored in full and thumbnail versions within the local user’s MessengerCache folder.
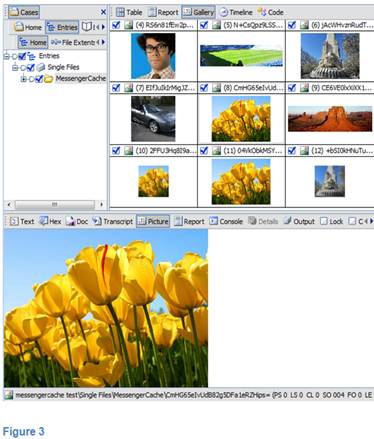
Figure 3 below illustrates a forensic examination of the local user’s MessengerCache folder. It can be seen that it contains the Remote User Tile and Remote User Theme Picture together with three different versions (they differ in resolution) of the Tulip picture. At this point none of these five pictures were solicited or accepted by the local user.
In the case referred to the prosecution, after discussions at court, offered no evidence in respect to all the counts on the indictment that relied on the pictures located within the MessengerCache folder. The defendant pleaded guilty to one count of possession not related to the MessengerCache pictures.